In a previous blog, we wrote about the benefits that come with Zeek-formatted metadata. This blog builds on that thread by discussing why our customers come to us as an enterprise solution to support their Zeek deployments.
The reason is best told through the experience of one of our government customers, which initially chose to deploy and maintain their own Zeek/Bro deployment. At the time, the rationale was reasonable: Use in-house resources for a one-time, small-scale deployment, and incrementally maintain it with the rest of the infrastructure while providing significant value to their security team.
However, over time, it became increasingly untenable:
- It was difficult to keep it tuned. Each patch or newly released version required the administrator to recompile a binary and redeploy.
- It became difficult to scale. While partially an architectural decision, sensors can rarely scale by default—especially those that push much of the analytics and processing to the sensor. We don’t see many deployments that can even operate at 3 Gbps per sensor. Over time, the sensors began to drop packets. The customer had to suddenly architect clusters to support the required processing.
- It was painfully difficult to manage legions of distributed sensors across multiple geographic locations, especially when sensor configurations were heterogeneous. When administrators who were familiar with the system left, a critical part of their security infrastructure was left unmanaged.
This no-win tradeoff drives many of our customers to ask us how their security teams can better spend their time. Manually administering tools (a.k.a. barely keeping afloat) in a self-managing fashion or being security experts and threat hunters? Consider the following comparison between a self-managed scenario and a Vectra deployment.
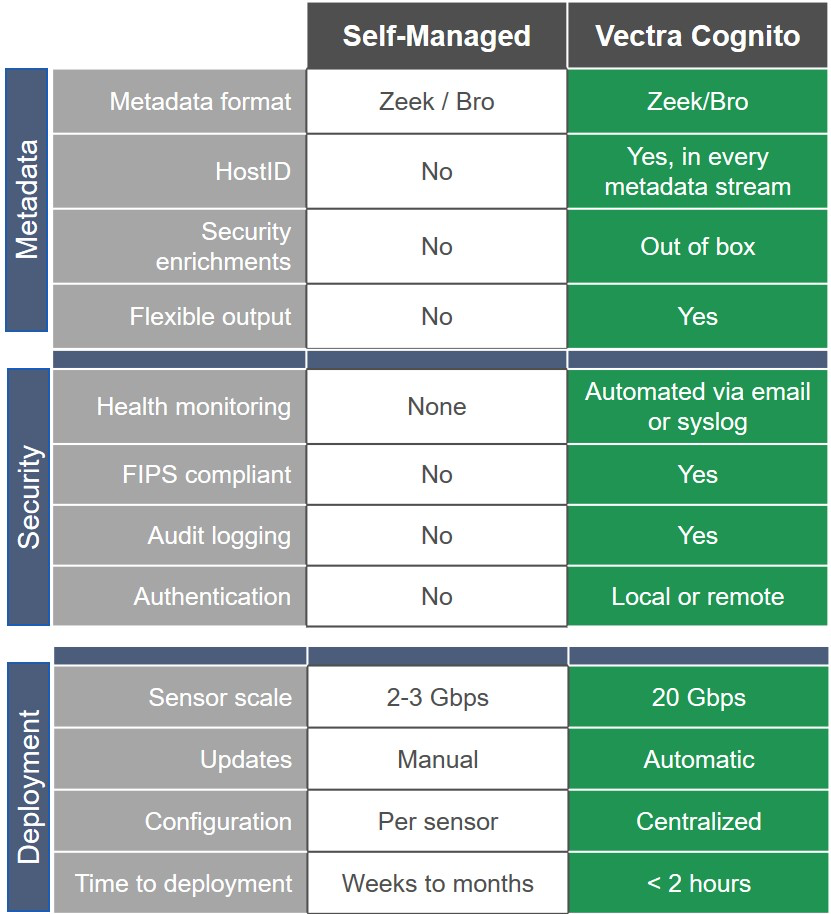
In addition to the deployment challenges shared by this customer, day-to-day operational requirements like system monitoring, system logging and even front-end authentication pose a heavy burden. Most make the choice to find a partner that can simplify the complexity of such a deployment: Accelerate time to deployment, enable automatic updates that eliminate the need to regularly patch and maintain, and perform continuous system monitoring.
These are default capabilities that free you to focus on the original charter of your security team. Think about your data capture and analysis architecture and deployment. We invite you to reach out to a Vectra representative for a consultative discussion about your deployment or to the authors of this Gartner research for more context about these issues.






