Recently we’ve had a lot of inbound requests to learn more about the hacking group, Scattered Spider. We've been studying them for a while now because if there is any threat group out there that represents the reason why we build our product, it's this group. They are nasty, they are bad, and they are bringing a lot of tools to the table that are really pushing defenders.
Today, we're going to walk you through who they are, some of the techniques they're using, and where they are in the world. Hopefully, this can help you understand the options available to defend against these types of attacks.
Who is Scattered Spider?
They are a currently active cyber-attack group that goes by a lot of names. You might hear them referred to as Starfraud, UNC3944, Scatter Swine, Octo Tempest, Muddled Libra, and of course, Scattered Spider. Scattered Spider is the top thing you're going to hear them referenced by now. They have heavily focused on developing playbooks that result in reproducible attacks that have high success rates. These attacks are mostly focused on identity.
We're seeing a lot of attackers using identity, but Scattered Spider has become very effective at coming up with ways to bypass MFA and get in through cloud identities. They ultimately transition into living-off-the-land attacks that span the gamut of the enterprise: cloud, network, everything that our identity touches, they're able to move through and interact with.
You'll often hear Scattered Spider mentioned in the same breath as ALPHV Blackcat. This is because they fall into the ransomware-as-a-service-affiliate group. ALPHV Blackcat is in its own space, which is separate from Scattered Spider, but it's intimately related to Scattered Spider and worth understanding. You can't talk about one without talking about the other.
What does Scattered Spider do?
These groups have a history of traditional and hybrid attacks on cloud enterprise environments. They are going to find ways to ultimately target data wherever it is the most valuable. This means there is no single area of the network or cloud that you need to be only looking at; the attacker is going after the entire environment.
And when we talk about this attacker and what they're doing, this is a ransomware group. They have a ransomware strategy that is focused on denial of service and extortion for stolen data. Denial of service in this context isn't DDoS. It's not just breaking things down. It is shutting down operations from the inside by encrypting systems, blocking access, and making it hard to do business because of their actions. Ultimately, they take the data off-site and demand payment or threaten to put the data out into the world/ use it against you. It is full extortion on top of the denial of service.
There are a lot of ransomware actors out there, but Scattered Spider is getting a lot of attention because of their association with ALPHV Blackcat, which has some of the highest ransomware demands seen in the current landscape.
Ransomware as a business model
Scattered Spider is a group of attackers. They are the ones running the attacks. They are a part of a ransomware business model where they act as an affiliate of a provider that gives them tools and techniques to run and drive an attack. This is why ALPHV Blackcat often gets mentioned in the same breath, because this is their provider of tools and there's an intimate relationship between affiliate and provider.

There’s a third party that's also sitting on the side of an identity access broker who adds to the mix, but ultimately Scattered Spider is the one driving these attacks. Scattered Spider has their own tools, but they also leverage off-the-shelf control points, these technologies that the provider does. The provider is ultimately the one who does the negotiations and manages the leaked data. So, there's a very intimate relationship between the two parties.
The current state of ALPHV Blackcat and its impact on Scattered Spider
Because of this ongoing relationship, there have been some shifts in what we expect Scattered Spider to do in the near term. ALPHV Blackcat effectively disappeared from the market, at least in name, when they were taken down by FBI operations. However, that didn't stop them from existing as a ransomware provider. Their website went down but they came back up, and once they came back, they were immediately involved with the Change Healthcare incident.
What ultimately happened was money was transferred/ ransomware was paid, and ALPHV Blackcat took the money associated with the affiliate and ran. Normally there's some payout to the actual ransomware executor, but ALPHV Blackcat ran and went underground. What normally happens in these cases is the attacker ends up rebranding, and the tools come out a different way. All that said, there are likely to be shifts in how Scattered Spider operates/specific tools they use.
From Vectra AI’s perspective, we've seen similar ransomware actors in the past, and various SaaS services that are in the ransomware space and are well-versed in how they operate. Because of our focus on behavioral coverage, Vectra AI remains very effective at detecting the core techniques that any ransomware provider would be using. This includes other vendors in the market for these ransomware tools, absent the core functionality that Scattered Spider as a group has developed on their own.
Cloud-centric Scattered Spider attacks
Let’s walk through some of the documented examples of what these attackers are, and what this group is doing to understand the sophistication involved.

In this attack, Scattered Spider started with an identity compromise using SMS phishing and SIM swapping. This is a technique that effectively allows an attacker to bypass MFA and log into an identity. There are a few other ways they've done this, but this is one effective way that has worked well for this group and some of the other active threat actors out there.
While there are indications of the sign-on being suspicious, and ways to detect this, SMS phishing is a path that allows access, and can bypass prevention, and they’re able to sign on. In this scenario, they get access to an Azure admin account and immediately pivot and start interacting with Azure and discovering the landscape. Next, they’re interacting with different tools in the Azure platform. They start putting tools onto available endpoints, VMS that were deployed in Azure, to effectively do recon from the platform-as-a-service angle.
This all leads to the attacker mapping out a path from the actual IaaS itself. Because there's a functionality in Azure (really in any Microsoft kind of deployment of VMs) called a serial console, they were able to run arbitrary code on the AVM. It’s essentially a remote management tool. This enables the attacker to run commands like a reverse SSH from any of the endpoints that are VMs in that Azure cloud.
What started as an identity compromise has now moved into the cloud, and then moved from the platform-as-a-service component into the IaaS piece, from which their traditional ransomware functionality comes into play. C2 is deployed, lateral movement over RDP connections is happening, privilege escalation, and traditional tactics that we see in ransomware actors as they move through a network, all are now in play after this more nuanced cloud infiltration. This ultimately leads the attacker to commit data theft and leaves an even greater impact.
Scattered Spider cloud attack path – a defender view
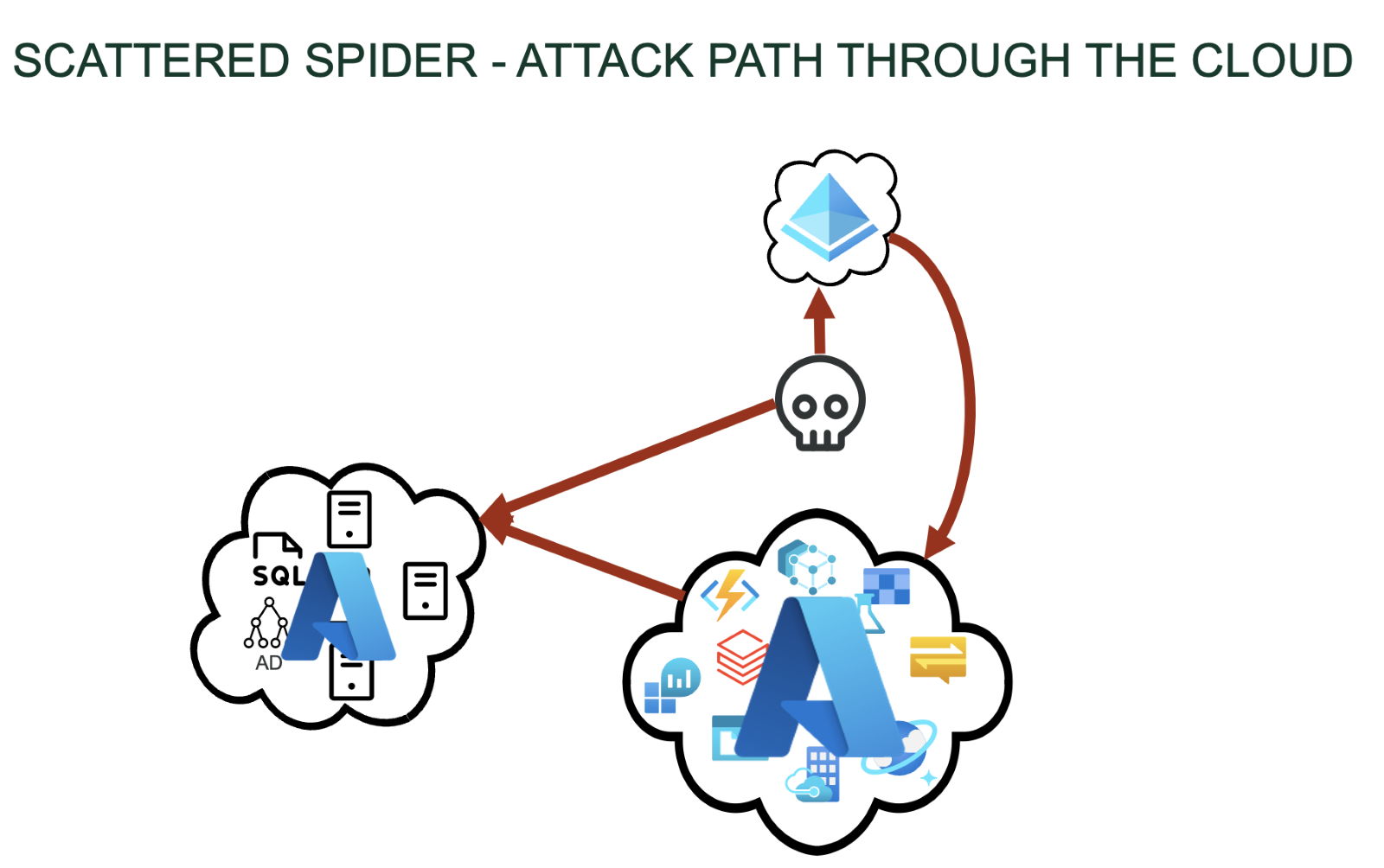
Here’s a more zoomed-out view of what just happened. We have our skull in the middle which represents the attacker. They hit the Entra ID identity through SMS phishing. They use that to pivot into Azure platform-as-a-service and use that platform-as-a-service to connect directly to Azure IaaS where they can deploy the command and control that brought the attacker into the IaaS. They're able to span multiple attack surfaces throughout their attack with minimal prevention that can stop them. And this is the type of attack, not the only one, but the type of attack that represents the techniques that are coming into play. The identity in this example was just one of Scattered Spider’s techniques.
Scattered Spider is highly effective at accessing and abusing identity
The diagram below shows a few different views of the documented cloud identity techniques. There is the traditional MITRE view of the identity techniques Scattered Spider has available to them in the cloud: SIM swap, MFA bombing, voice phishing, etc. They register persistence once they've bypassed MFA and they can do it at the device level, and the tenant level. They can manipulate accounts and start harvesting data. Ultimately, it's not just identity tactics at play, they span the gamut of the attacker's space.

Full MITRE ATT&CK view of Scattered Spider
The key arcs to note here center around living off the land: using identity to pivot between the areas they're interested in and enabling persistence. They are running the standard ransomware playbook that we’re familiar with like using C2 channels a lot of times with commercial remote access tools or third-party software. They're not developing crazy payloads; they don't need to. Instead, they're using an off-the-shelf ransomware-as-a-service model with tools that have been validated in other places. They're running things like Mimikatz, using lateral movement, RDP just like any other ransomware actor, and AD where they're going after Impact/Exfil, that’s their playbook.

Vectra AI’s MITRE ATT&CK cloud identity coverage for Scattered Spider
Vectra AI has been watching Scattered Spider for a while. We've been monitoring ransomware groups in this ransomware-as-a-service activity for some time now and our coverage has been effective in these types of attacks. For perspective, this is the identity matrix that relates to our coverage.

Vectra AI has full coverage from the cloud side for identity. This includes everything from the registration to the domain trust manipulation to the access events, etc. We've been able to build coverage that has a real impact on pinpointing the attacker and what they do. To give you an idea, here are some examples of relevant cases to this attack space.
Attack Example 1
This is an anonymized attack that we saw that’s reminiscent of the techniques documented in these initial events of a Scattered Spider attack.

The attacker appears to perform targeted phishing. It may have been a phishing kit that enabled them to bypass MFA: another kind of sellable software that exists out in the market. They signed in through the Entra ID account and were moving to add persistence. That means they would register a device because if you steal just a token, you only have temporary access to it.
This was an actual case that was identified by the Vectra MDR service. It was seen in the first 5 minutes of the attack and shut down. The attacker would’ve had many opportunities to cause havoc if this had been successful, but because of Vectra AI‘s visibility, we were able to stop this incident.
Attack Example 2
Here is another, more nuanced example of an attack.

This attack involved an attacker driving through voice phishing essentially to lead to a password reset. There are other reports of this being a Scattered Spider technique, but even when that happens, there are aspects of that sign-in that are identifiable as suspicious. There's an opportunity to alert on that axis event, but ultimately in all these cases we see, attackers don't do just one thing and Scattered Spider is no different.
You’ll then notice access into Exchange, moving through SaaS apps as they move into the M365, and then start to put redundant access at the federated trust level with an admin-level account, and probing into Azure. The opportunity was there is there to stop it because this organization had the right visibility. But you can see everything from anonymous access, into an Azure VMA technique to evade detection, then Exchange persistence, delegating access to be able to manipulate accounts in that domain, interactions with SharePoint, turning federated trust for persistence, in this case, the broader Azure cloud was available to the attacker. Luckily, this organization had the right tools in place so the attacker could be stopped before the impact happened.
Full MITRE ATT&CK view of Scattered Spider with the Vectra AI Platform
Vectra AI provides cloud, network, and identity coverage for Scattered Spider (and similar attacks). Highlighted in green are the areas that are covered by Vectra AI.
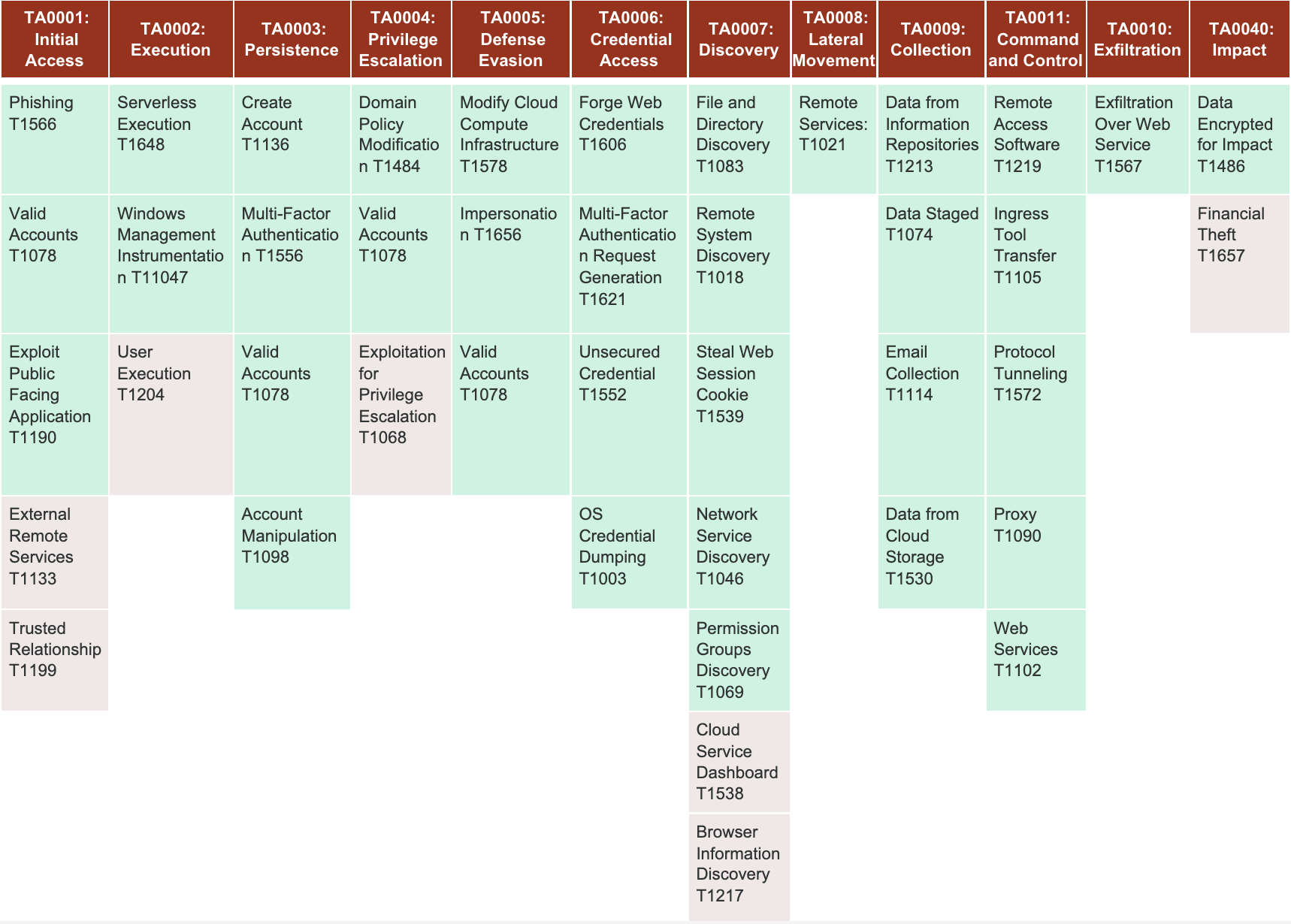
Given the diversity of this kind of attacker, it’s vital to have both visibility from the identity stage, and the cloud stage to the actual kind of network components as well as clarity once you have that coverage.
That's where Vectra AI’s prioritization comes into play: coordinating disparate signals into one clear signal and giving clarity to any of those pivots happening between the network and the cloud.
Then, from a response side or control side, you know there's an opportunity to leverage either the Azure AD integrations to disable the accounts, the AD on the network integration to disable the accounts, EDR integrations to disable the endpoint, or any of the broader vector response functionalities to take immediate action.
For more details, watch the complete Scattered Spider threat briefing.
For more information on the Vectra AI Platform, check out the following helpful resources:
- Vectra AI Platform
- Take an Interactive Tour






